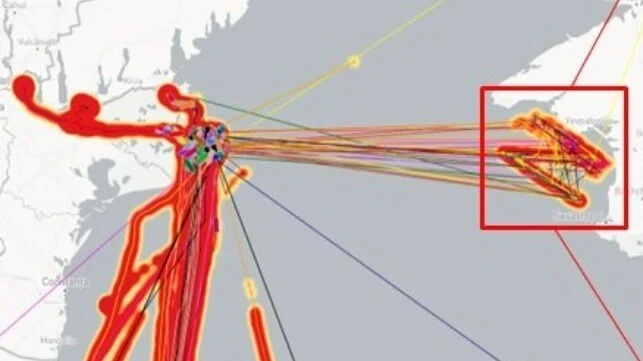
La firma de inteligencia geoespacial Geollect ha identificado un patrón AIS (Automatic Identification System) falsificado que traza el símbolo “Z” de la invasión rusa de Ucrania en una posición frente a la costa de Crimea. Es el último de una larga serie de incidentes de suplantación de identidad en la región, y el patrón se ha atribuido durante mucho tiempo a los actores del gobierno ruso. La suplantación remota de GPS puede engañar a una unidad receptora de GPS para que calcule una ubicación falsa. Entre otras aplicaciones, esta forma de interferencia de señal se puede utilizar para derrotar los sistemas de guía GPS de ciertos drones y armas de precisión fabricados en Estados Unidos y la OTAN. Según los informes, Rusia es competente en esta forma de guerra electrónica.
Geospatial intelligence firm Geollect has identified a spoofed AIS pattern tracing out the “Z” symbol of the Russian invasion of Ukraine at a position off the coast of Crimea. It is the latest in a long string of spoofing incidents in the region, and the pattern has long been attributed to Russian government actors.
Remote GPS spoofing can trick a GPS receiving unit into calculating a false location. Among other applications, this form of signal interference can be used to defeat the GPS guidance systems of certain U.S.- and NATO-made drones and precision weapons. Russia is reportedly proficient in this form of electronic warfare.
There is a long history of GPS spoofing near Russian and Russian-occupied areas of the Black Sea coastline, and it periodically affects shipping. Since a ship’s AIS transponder broadcasts the location it receives from the ship’s GPS unit, a broad-scale GPS spoofing attack will displace the “location” that the ship broadcasts via AIS, producing results that can sometimes appear bizarre. In 2017, more than 20 ships reported that their GPS positions had been erroneously relocated 25 nm inland to the airport in Novorossiysk. Others at anchor appeared “clustered” in areas where there were no radar returns for ships.
Over the course of 2017-19, non-profit analytics group C4ADS catalogued about 10,000 similar incidents affecting 1,300 vessels, most in or around areas of Russian influence. The report also drew a correlation between the movements of Russian President Vladimir Putin and the mass spoofing events, noted contributor and cybersecurity expert Dana Goward.
In June and July 2021, three NATO warships – the Royal Navy’s USS Defender, the U.S. Navy’s USS Ross and a Royal Dutch Navy vessel – all had their locations spoofed to positions off Russian-occupied Crimea. The reason and culprit remain unknown.
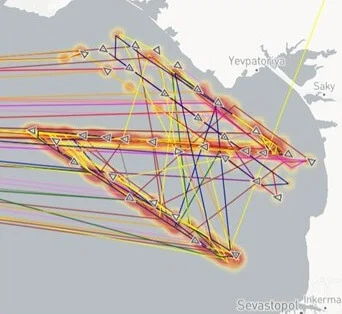 This month, a large number of merchant ships along the southern coast of Ukraine had their AIS locations remotely spoofed to the coastal waters of Russian-occupied Crimea. However, instead of a random pattern or a cluster, the AIS positions form a clear “Z” shape, the de facto symbol of support for the Russian invasion. This AIS spoofing pattern was almost certainly created by transmitting false AIS signals, mimicking the ships’ actual AIS transmissions with corrupted duplicates, according to Geollect.
This month, a large number of merchant ships along the southern coast of Ukraine had their AIS locations remotely spoofed to the coastal waters of Russian-occupied Crimea. However, instead of a random pattern or a cluster, the AIS positions form a clear “Z” shape, the de facto symbol of support for the Russian invasion. This AIS spoofing pattern was almost certainly created by transmitting false AIS signals, mimicking the ships’ actual AIS transmissions with corrupted duplicates, according to Geollect.
“It is highly likely that this is a deliberate information operation by a pro-Russian actor (possibly Russian military psychological operations) ahead of an anticipated Ukrainian counteroffensive and/or in celebration of Russia’s proclaimed victory over Bakhmut,” assessed Geollect.
The pattern began to show up on AIS on the 14th, and strengthened from May 19-21. Putin declared victory over Ukrainian forces in Bakhmut on May 22. In a clear sign of spoofing, merchant vessel “speeds” between these erroneous AIS positions were as high as 100 knots, Geollect reported.
Fuente: https://maritime-executive.com